The White House recently released a memorandum detailing requiring zero trust architecture and detailing zero trust best practices. This establishes a federal zero trust architecture strategy, mandating that agencies meet certain cybersecurity requirements and objectives by the end of 2024. Zero trust architecture is a key part of the federal technology infrastructure, safeguarding against threats to public safety and privacy. Read on to learn more about zero trust best practices and how your agency can comply with the new regulations.
Introduction to Zero Trust
Zero trust refers to the developing set of cybersecurity criteria that advance defenses from a reliance on fixed, network-based perimeters to instead target users, assets, and resources. Zero trust diminishes uncertainty when making privilege access decisions, particularly for IT systems and services existing in a compromised network. Zero trust architecture utilizes zero trust precepts to structure industrial infrastructure and workflows, ceasing to assume implicit trust or grant access to users based on their network or physical location. With a zero trust framework, implicit trust and access will not be granted based on ownership, either. Instead, to access an enterprise resource with a zero trust framework, both the subject and the device must be authenticated and authorized beforehand. The main focus of zero trust is safeguarding resources rather than network segments. Consequently, zero trust architecture protects assets, workflows, services, and network accounts rather than just the network location, focusing security around resources rather than locality.
Memo Summary and History
In the wake of cyberattacks like the Colonial Pipeline ransomware attack and the Solar Winds hack, the U.S. government has stepped up efforts to strengthen its cybersecurity systems. The Colonial Pipeline, which controls a large portion of the United States’ energy infrastructure and provides fuel to much of the East Coast, fell under cyberattack in the spring of 2021. The Solar Winds hack in late 2020 also revealed weak points in the global software supply chain, impacting federal and private-sector computer systems. Both of these crises called attention to major chinks in the nation’s cybersecurity armor, revealing the lackluster security and ruptured authority between government liaisons and the private sector. Additionally, a newly discovered Log4j vulnerability has also left organizations, governments, and individuals open to attack, making it easier for cyberattackers to break in and steal sensitive information or install malicious software. Consequently, the U.S. government has sought to bridge these gaps by shoring up its cybersecurity defenses, and one of the primary ways in which they’re protecting their sensitive data is by implementing zero trust architecture.
Memo Highlights & Zero Trust Best Practices Analysis
Implementing zero trust migration plans will require government agencies to shift from siloed information technology services to collaborative and cooperative zero trust frameworks. This gradient of implementation is represented best on the Cybersecurity and Infrastructure Security Agency (CISA)’s Zero Trust Maturity Model, delineating one of the primary paths bolstering the transition to zero trust.
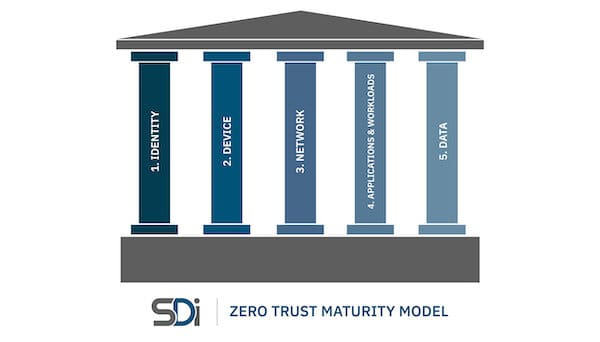
The Model outlines the five pillars of zero trust: identity, device, networks (and environment), applications and workloads, and data. These are the cornerstones of effective zero trust architecture. However, agencies and organizations do not need to optimize for every pillar simultaneously; the Model is transitional, constructed so implementers can work up to full integration across pillars. To illustrate this process, the Model includes stages, beginning at the Traditional Stage encompassing traditional cybersecurity practices, moving to the Advanced Stage, and finally the Optimal Stage.
Consequently, as implementers’ policy enforcement decisions become more effective, they will increasingly rely on automation. The Model is constructed so each pillar can progress on its timeline, but the ultimate goal is cross-pillar integration. The stages’ progression from traditional, to advanced, to optimal, delineates the transition from manual configuration to full automation. By gradually evolving to zero trust, the Zero Trust Maturity Model distributes costs evenly while still ensuring compatibility.
Identity
As the first pillar of the Zero Trust Maturity Model, the identity pillar targets the individual. At the Traditional Stage of CISA’s Zero Trust Maturity Model, agencies typically only perform a limited risk assessment that prioritizes password and multifactor authentication (MFA). Now, password policies cannot mandate the use of special characters or consistent rotation. At the Advanced Stage, multifactor authentication is still in place (at the application layer), but agencies must move towards a degree of identity organization using cloud and on-site systems.
Agencies are prompted to aim for increased use of passwordless MFA, helping to revamp and automate their authentication protocol. Additionally, agencies are encouraged to discontinue outdated authentication systems that are ineffective against phishing, use one-time codes, prompt push notifications, or any other outmoded verification measures. This step is particularly important because such agencies may be profitable targets for phishing attacks. However, this risk is easily mitigated through the use of phishing-resistant tokens such as personal identity verification (PIV) cards.
At the Optimal Stage, implementers aim for continuous validation and real-time machine learning analysis, achieving full automation. For federal agencies and the military, the implications of identity requirements are even more far-reaching, requiring them to update their password policy and eventually implement passwordless MFA. Additionally, they are expected to implement attribute-based access control, helping to protect sensitive information from cyberattackers.
Devices
Devices are the second pillar of the Zero Trust Maturity Model, typified at the traditional level by limited visibility into compliance and simple inventory. At the advanced level, agencies must employ compliance enforcement, and data access must depend on device posture on first access.
When controlling access to agency resources, enterprise authorization systems must try to integrate at least one device-level signal along with user identity information. The optimal level requires constant device security monitoring and validation. At this stage, data access is dependent on real-time risk analytics. The federal government keeps a total inventory of each device operating and authorized for government use, meaning they can prevent, identify, and react to incidents on all government devices. Thus, device requirements for DoD agencies imply that they must implement CISA’s Continuous Diagnostics and Mitigation (CDM) program to effectively protect government networks and systems. Additionally, they must integrate CISA-compliant endpoint detection and response (EDR) tools, maximizing their ability to detect malignant cyber activity on government networks.
Networks and Environment
Networks and environment constitute the third pillar. In the Traditional Stage of CISA’s Zero Trust Maturity Model, agencies often start with large macro-segmentation and minimal internal or external traffic encryption. To move to the Advanced Stage of the Model, enterprises should encrypt all domain name system (DNS) appeals and environmental HTTP traffic. They should also create a plan to split up their perimeters into isolated environments.
The movement to the advanced stage is defined by ingress (inbound) and egress (outbound) micro-perimeters and basic analytics. However, governmental applications must not rely on network perimeter protections alone. Instead, users ought to log into the applications themselves instead of the networks, protecting against unauthorized access. The Optimal Stage requires full distribution of ingress and egress micro-perimeters, machine learning-based threat protection, and the encryption of all traffic.
The implications of network and environment requirements for DoD agencies mean they must encrypt DNS and HTTP traffic, encrypt internal data movement (or balance with network monitoring tools), encrypt email (which will likely be more challenging for external email), and create an enterprise-wide architecture and isolation strategy.
Applications and Workloads
The fourth pillar of the Model deals with applications and workloads. At the Traditional Stage, agencies’ access is based on local authorization, minimal workflow integration, and a low degree of cloud accessibility. The Advanced Stage requires centralized authentication-based access and basic workflow integration. But at the Optimal Stage, access must be authorized continuously with strong workflow integration.
CISA recommends that agencies dissect their applications the same way that the U.S.’s adversaries do, rather than just beefing up internal testing programs. To comply with applications and workloads requirements, DoD agencies must enhance testing through a dedicated Application Security Testing Program or utilize high-quality firms specializing in application security for independent third-party evaluation. DoD agencies must also aim for an immutable workload via DevSecOps, managing patches centrally while trying to avoid patches entirely. Additionally, it appears that agencies must have at least one internal application hardened as though publically available, if not literally publically available. This can be achieved through penetration testing.
Data
The final pillar of the Zero Trust Maturity Model is data. At the Traditional Stage, data is not well inventoried, typified by static control and a lack of encryption. A movement to the Advanced Stage requires agencies to implement least privilege controls and encrypt data stored in the cloud or remote environments when at rest. Agencies can rely on the cloud and its audit logs; even if the agency’s environment is jeopardized, the cloud still offers protection for keys and decryption operations. The cloud is also integral in the Optimal Stage, typified by dynamic support and encrypted data.
To comply with new data regulations, DoD agencies must comply with the upcoming zero trust data security guide for agencies and implement initial automation of data categorization and security responses by focusing on tagging and managing access to sensitive documents. Agencies must also audit access to any data encrypted at rest in commercial cloud infrastructure, collaborate with CISA to implement comprehensive logging and information sharing capabilities per OMB Memorandum M-21-31.30, and implement centralized logging.

Talk to Sentient Digital About Zero Trust Best Practices Today
CISA’s pre-decisional draft helps to provide an introductory framework for the Zero Trust Maturity Model, contextualizing the government’s decision to implement zero trust architecture as a cornerstone of their infrastructure. CISA’s Zero Trust Maturity Model breaks down how to achieve optimization through incremental advancements, creating a framework to aid in the transition to zero trust architecture. As agencies move towards a zero trust model, their cybersecurity solutions will increasingly rely on automation, promoting more thorough integration and creating opportunities for more dynamic policy enforcement decisions.
To learn more about getting started with zero trust architecture, look to CISA’s Zero Trust Maturity Model: Pre-decisional Draft. This document provides steps to help agencies implement zero trust migration plans, making it a valuable resource for affected agencies.
Reach out to the experts at Sentient Digital for additional advice about getting started with zero trust architecture. With extensive industry knowledge and years of experience, Sentient Digital provides valuable assistance. Although the migration plan may be complex, with our expert guidance, your agency can meet the requirements in no time. Contact us today to learn more about how your agency can incorporate zero trust architecture using zero trust best practices.




