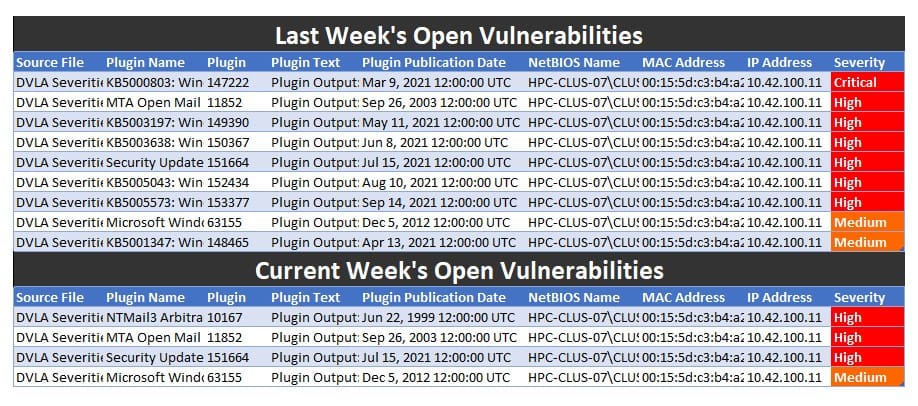
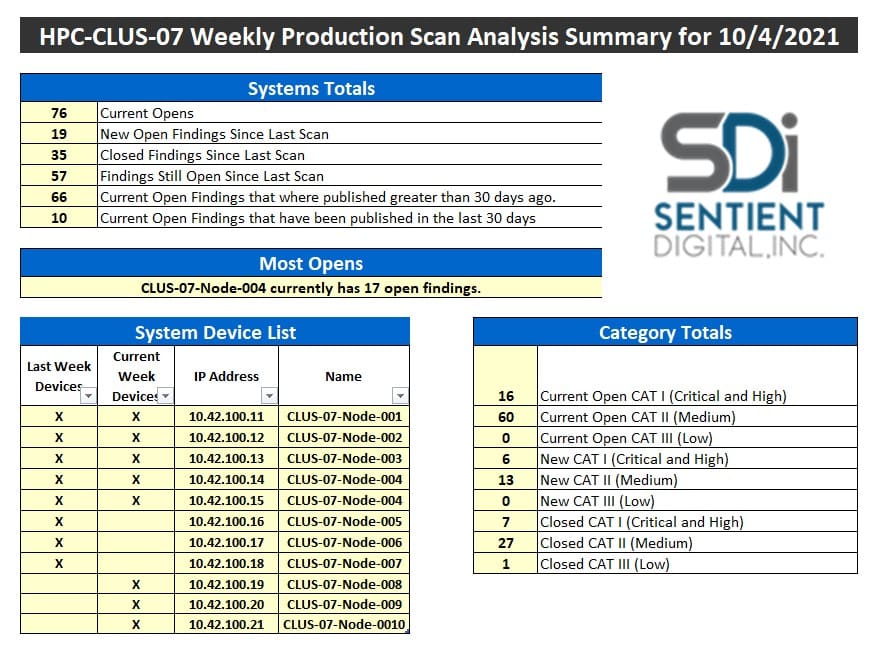
What Does Your Raw Vulnerability Data Look Like?
Performing Extract, Transform, and Load (ETL) operations on raw vulnerability data is a time-consuming and resource-intensive process to import and format information from various sources into an output that is ready for analysis. With varying types of devices (Windows, Linux, Cisco) and different classification levels (Unclassified/Classified), cybersecurity analysts and engineers need fast, reliable tools to format this data for review.