In a time when workspaces continue to digitize alongside a rise in cyber attacks, effective security engineering services are needed to keep your organization (and its sensitive information) safe from cyber threat. Practical and forceful security engineering will help you maximize the value of your technology investments, optimize operations, ward off cyber attacks, and increase productivity, all the while reducing costs and downtime. Navigating the complexity and the integration needed to maximize your cybersecurity systems can be a major barrier to implementation, hindering innovation and making your network infrastructures more vulnerable to cyber attack. However, with the help of IT experts, you can develop an effective cybersecurity strategy with state-of-the-art technology (and without the hassle of having to do this on your own).
Read on to learn which security engineering services your organization should consider and the benefits of keeping your cybersecurity on the cutting edge, no matter your industry.
Network and Systems Security Engineering Services
As the demand for digital networking increases, optimizing your network infrastructure and system services is paramount. This is where a network system engineer comes in handy. By documenting and detailing systems interactions, a network engineer can determine root causes and effective solutions while also evaluating and recommending new technologies. This helps your organization to optimize network performance and operational efficiency while also keeping abreast of new technology developments. Effective network and systems engineers also account for client security updates such as hotfixes and antivirus software, enforcing IT infrastructure standards.
By integrating satellite, wireless, virtualization, and sensors into your network configuration, network and systems engineers can increase your interoperability, helping software and hardware to operate in tandem. This creates a more stable and consistent interface that works better for you and your organization, assuring that new information is disseminated efficiently and securely the first time around. By stabilizing both your software and the Internet of things (IoT) (or the network of physical objects embedded with sensors, processing capabilities, and software that help your business operate), your organization can protect itself from common and emerging cybersecurity threats. And as mobile technology such as cell phones and smart watches become even further integrated into our lives and businesses, it is crucial to account for IoT and IoMT devices in our solutions.

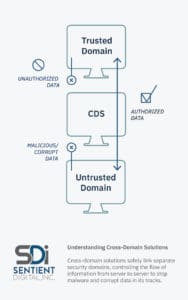
Cross-Domain Solutions
A Cross-Domain Solution (CDS) is a type of controlled interface that allows you to manually or automatically access and/or transmit data between distinct security domains. A CDS is, effectively, a boundary whose mechanisms implement security standards and control the flow of data between linked information systems, ensuring the security of trusted network domains as they transfer information. Cross-Domain Solutions are especially important for organizations that function in risky environments (such as military or intelligence operations). These high-risk conditions necessitate a more aggressive approach to security engineering services, often calling for high-assurance security and state-of-the-art content filtering to safeguard against data breaches and data corruption.
Protecting fixed format data accessed from sensors and artillery, telecommunications streaming data, and complex data such as PDFs, office documents, and email messages, a CDS provides ironclad network integrity and data confidentiality for a wide range of sensitive information. Cross-Domain Solutions are safer and more secure than firewalls. So while firewalls provide sufficient security for everyday commercial organizations, they are more flawed and vulnerable to exploit. A CDS’s hyper-specialized hardware and software provides the highest degree of security for high-risk operations contending with extremely sensitive data.
However, you don’t need to be a high-risk government operation in order for a CDS to work for you. Commercial, industrial, and utility organizations can also benefit from the impenetrable security offered by a CDS, protecting hardware, operating systems, and sensitive information. Since a CDS allows business to flow efficiently between separate systems, while still maintaining a high level of protection, commercial Cross-Domain Solutions allow organizations to construct a very strong network while still making information easy to access within company parameters. This way, businesses can operate efficiently and effectively while minimizing the threat of malware and data leaks.
Certification and Accreditation Services
Certification and Accreditation (C&A) services vet and authorize an IT system, like a CDS, to ensure maximum compliance and security once a system is operational. The certification aspect includes the trial and assessment of both the technical and nontechnical aspects of the security system in order to evaluate its compliance with industry security standards. The accreditation is when a certified management official authorizes an IT system to function in accordance with industry standards, keeping risk at a tolerable level. Effective C&A services evaluate security and compliance processes to ensure maximum operability, keeping your technology running safely and smoothly while mitigating cybersecurity threats. The identification and articulation of both short term and long term vulnerabilities can help your organization optimize risk management and ward off potential breaches. By assessing the vulnerabilities of IT systems and pinpointing liabilities on the front end, C&A engineers perform proactive cybersecurity rather than reactive cybersecurity, ensuring that your organization’s security weaknesses are identified and addressed before an attack occurs. Reactive cybersecurity will cost you more money on the backend, so it is important to get the experience and expertise needed to walk you through C&A processes the first time around. By working collaboratively with accredited experts, organizations can develop a time-efficient and cost-effective strategy for C&A completion, ensuring that your IT systems are as secure as possible.
Well-Defined Service Management Processes
Well-defined service management processes are crucial to effective implementation and maintenance of your IT system. To preserve the complex infrastructure of your diagnostic service (and provide mission-focused solutions), IT services like Sentient Digital operate within industry frameworks such as the Information Technology Infrastructure Library Framework.
Information Technology Infrastructure Library Framework
The Information Technology Infrastructure Library (ITIL) is a framework used to manage IT services, helping to codify and define the relationship between security engineering services and the business who hire them. The ITIL system proposes best practices for executing the five stages of the IT service lifecycle:
- Service Strategy
- Service Design
- Service Transition
- Service Operation
- Continual Service Improvement
The first step of the process, service strategy, involves getting to know your IT customers and understanding how to meet their service needs. Developing a strategy for development, delivery, and support is crucial to ensure that cost of service and value delivered are equitable. This step gives both the engineers and the customers a more holistic understanding of the manpower and resources needed for the job, ensuring transparency and candid execution.
Next, the service design portion of the process ensures that services are tailor-made to fit each customer and their needs. During this step, the engineers plan out the technology and architecture needed to time-effectively and cost-efficiently meet the needs of the client.
Then, in the service transition phase, the architecture finalized in the service design step is constructed, tested, and shifted into production. Tests are performed and transitions planned to make sure that users, support personnel, and the production setting are readied for the shift into production.
After transitioning into the service operation phase, the operators perform the service on an ongoing basis, monitoring the health and efficacy of the program by handling disruptions, diagnosing root causes of system issues, charting trends connected to chronic issues, and controlling service access.
The final stage of the IT service lifecycle is continual service improvement (CSI). This stage structures a process by which the IT provider can calculate and optimize the service levels, the technology, and the efficiency of the service program, delivering long-lasting value and attentive service.
This framework helps IT organizations deliver consistent and effective service while retaining the flexibility required for personalized service. The ITIL approach to service management accounts for nuance without sacrificing efficiency, giving IT companies and their customers the best of both worlds.

Talk to Sentient Digital About Security Engineering Services Today
Researching ways to protect your organization? To implement the latest solutions and security engineering services without the hassle, reach out to the specialists at Sentient Digital. Sentient Digital’s managed services build on the company’s strong foundations, combining engineering savvy and support experience to create a flexible and scalable program tailored to each client. With our deep industry knowledge and mission-focused service, we provide cost-effective tools and assistance. Contact us today to learn more about our tailored security engineering services.
Looking to join a team of cutting-edge technology professionals? Sentient Digital is proud to employ a brilliant team of scientists and engineers, all of whom work closely with businesses, the military, and government agencies to help these organizations maximize the security and efficiency of their systems. We’re looking for team players with a growth mindset who are ready for a challenge. Additionally, we offer competitive benefits and exciting chances to perform innovative work spanning from cybersecurity to systems engineering, and software development to IT support. If you’re a creative problem solver looking for rewarding work in a dynamic environment, browse our open positions for more information or contact us to start a conversation about your career.




