IPv6 is the present and future of the Internet, and the federal government has put in place an IPv6 mandate to ensure that its agencies adopt it. Effective June 29, 2021, the Department of Defense began its mandatory transition to IPv6, calling for all networked systems to switch to the most up to date version of Internet Protocol (IP), Internet Protocol Version 6 (IPv6), by the end of the fiscal year 2025. This change brings new potential cybersecurity issues. Recognizing this, the National Security Agency recently released guidelines to help the Department of Defense and other agencies’ networks use IPV6 safely.
With the internet growing everyday, the IPv6 mandate is geared towards modernizing the internet to keep up with industry trends, and as always when new federal technology mandates come into effect, federal agencies as well as organizations in other sectors need guidance on how to proceed. This guidance includes ensuring that agencies are prepared for the cybersecurity challenges they may encounter.
An Introduction to IPv6
An internet protocol is the principal communications protocol used for relaying information and identification for computers on networks across the internet. IPv6 is an internet protocol based on IPv4, developed to expand IPv4’s limited capacity for addresses available to sustain the internet and all the unique IP addresses from the devices connected to it. Since November 2019, there are no more IPv4 addresses to go around. IPv6 was created in the 1990’s as a response to this long-awaited outcome.
Among the features included in IPv6, some highlights are built-in support for multicasting (as opposed to IPv4’s broadcasting), in addition to a simpler header format and smaller routing tables. Multicasting’s advantage over broadcasting is a reduction in bandwidth, as a single packet can be sent to multiple destinations. Additionally, IPv6’s simpler header format decreases the amount of processing power required for each packet. The protocol’s smaller routing tables improve the efficiency of routing packets as well. These are examples of some of the features that make the potentially complicated transition from IPv4 to IPv6 beneficial for agencies and organizations.
Running an IPv6-only network means that users cannot access content or services that are still running over IPv4. Big tech players like Google, Facebook, and Apple have initiated global leadership in deploying IPv6, which has illustrated how content providers have also helped network providers to move their traffic onto IPv6. For example, as of 2021, T-Mobile’s network runs 91% of its internet traffic over IPv6 in the U.S.
Sticking to IPv4 comes at a cost. The concerns that once loomed over the switch to IPv6 have reversed; sticking with IPv4 is now what causes increases in cost and difficulties in deployment.
Limitless Space: IPv4 vs IPv6
The main difference between the two IPs is the extended space that IPv6 provides. In the same way that area codes were added to precede phone numbers, IPv6 accommodates the growth in internet use by adding a substantial number of IP addresses.
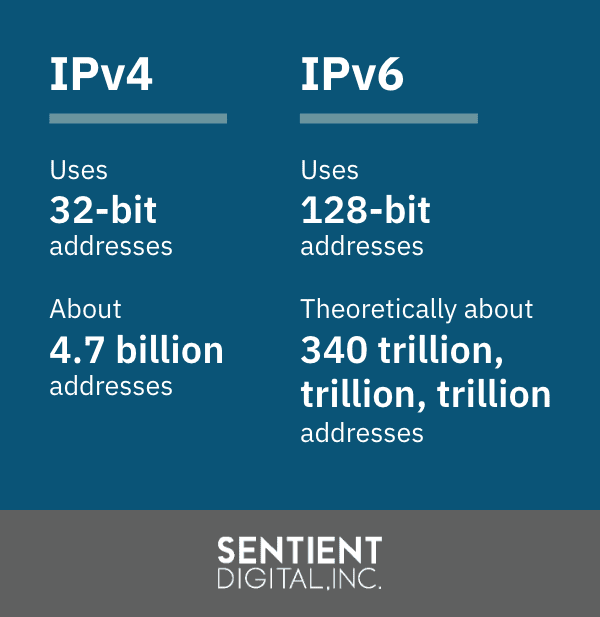
IPv4 was running into an unavoidable obstacle: address exhaustion. IPv4’s 32-bit addresses allow for only 2^34 combinations, which equals about 4.7 billion addresses. In IPv6’s superior 128-bit addresses, each bit corresponds to a ‘0’ or ‘1’, theoretically resulting in 2^138, which equals about 340 trillion, trillion, trillion addresses. End-users won’t notice when they are using IPv6 instead of IPv4, and vice versa. In terms of addresses, however, the two protocols do look different.
The actual amount of usable addresses is slightly less, as IPv6 addresses are structured for routing and other purposes with certain ranges reserved for special use. However, the total number of addresses is undeniably large. This expanded capacity enables a correspondingly large number of devices to connect to the internet, including phones, vehicles, and household appliances. This also means that we’ll never run out of IPv6 addresses. Additionally, beyond increased address space, Mobile IPv6 (MIPv6) is another enhancement over IPv4, as it was designed with mobile devices in mind, the ubiquity of which was not a part of life in the 1990’s.
The Transition from IPv4 to IPv6
The primary progress made from IPv4 to IPv6 is seen through three transition mechanisms: dual stack, tunneling, and translation. Firstly, IPv6’s dual-stack mechanism allows both IP adaptation to coexist on the same network and network devices, making it the most preferred, versatile way to deploy IPv6 in existing IPv4 environments for many network administrators. However, NSA points out that this requires the use of protective cybersecurity measures specific to both protocols.
Secondly, IPv6 can tunnel information contained in the IPv6 packets to IPv4 packets, either manually or automatically. Importantly, IPv6 allows for auto-configuration. When a device uses IPv6, it can independently configure itself when connected to other IPv6 devices, meaning that configuration tasks like IP address assignment and device numbering can be carried out automatically. Unfortunately, NSA’s 2023 guidelines, discussed below, recommend against the use of tunneling if at all possible, due to its inherent cybersecurity risks.
Thirdly, IPv6’s translation method allows for an IPv4 header to replace the IPv6 header of the packet. With the IPv6 packet transformed into an IPv4 packet, IPv6-only clients can exchange IPv4 devices and translate between private and public IPv4 addresses.
IPv6 trumps IPv4’s protocol with increased authentication and privacy measures. IPv6’s protocol is embedded by IPsec security, a built-in security framework that manages encryption and authentication between hosts without needing any applications on either host.
What happened to IPv5?
The jump from IPv4 to IPv6 might have you wondering what happened to IPv5. IPv5 indeed existed but never experienced widespread adoption. Like IPv4, IPv5 used 32-bit addresses that also offered limited IP addresses and thus no solution to the rapid depletion of IP addresses that IPv4 ran into. IPv5’s purpose was to support voice and video across IP networks for connection-oriented communications. Although IPv5 accomplished this task, it was only used experimentally because of its limited address capacity. Its contributions nonetheless led to the eventual adoption and development of the protocol that came to be named IPv6.
What Is The Federal Government’s IPv6 mandate?
The Office of Management and Budget issued OMB Memorandum M-21-07, dated November 19, 2020 requiring all federal agencies to stop using IPv4 and transition to IPv6.
In order to facilitate this change within the Department of Defense, the DoD issued a memorandum effective June 29, 2021 to ensure that “all new networked DoD information systems that use (IP) technologies will be IPv6-enabled before implementation and operational use by the end of 2023” and provides a staged plan towards full IPv6 implementation by the end of 2025, similar to that contained in the OMB memorandum. IPv6-enabled information systems are systems in which the use of IPv6 is “turned on” for production use. Per the DoD memorandum, the Digital Modernization Infrastructure Executive Committee (DMI EXCOM) will serve to govern and enforce IPv6 transition efforts at the DoD level, essentially taking on a project management role.
The DoD’s IPv6 implementation plan includes incremental milestones of 20%, 50%, and 80% of IP-enabled assets on Federal networks operating in IPv6-only environments by the end of fiscal years 2023, 2024, and 2025. Additionally, the DoD will phase out any systems unable to convert to IPv6.
The overarching purpose of the IPv6 mandate is to ensure all Federal information systems and services transition to IPv6 by the end of the year 2025. The Federal Energy Regulatory Commission (FERC) will facilitate the government’s commitment to keeping up-to-date with the state of the industry. FERC has brought together acquisition, policy, and technical team members to create an agency-wide IPv6 integrated project team. The IPv6 mandate applies to all FERC information, information systems, employees, contractors, and all other users of FERC information and information systems.
How does an agency coordinate the process for complying with the IPv6 mandate?
IPv6’s extended address space is the only practical way to accommodate and keep up with the ever-growing need for IP addresses. Whether you are a content provider, network operator, or developer, it’s critical that you connect to the internet using IPv6. A study of how FERC manages its process may help you understand how to structure leadership of the transition process.
The FERC policy strategy lays out the roles and responsibilities for FERC’s Executive Director (ED), Chief Information Officer (CIO), Chief Information Security Officer (CISO), Information System Owner (ISO), Information System Security Officer (ISSO), and FERC Cybersecurity and Information Assurance Division (CsIA).
FERC’s ED has overall responsibility for compliance with the OMB memorandum and issuing agency-level guidance on that subject. The CIO will take charge of cybersecurity-related implications of the memo, such as setting IT policy and approving IPv6 waivers, while delegating some information security responsibilities to the CISO, whose role includes facilitating communication between the CIO, ISO, and ISSO. Among the ISOs responsibilities are the procurement, development, integration, modification, operation, maintenance, and disposal of an information system, and the creation of a security plan. The ISSO role entails inventory, monitoring, and alert response functions, among others. Finally, FERC’s CsIA will evaluate the results of remediation efforts and provide assistance to the ISO and managers.

Cybersecurity Risks of IPv6 and the 2023 NSA Guidelines
Although the transition to IPv6 brings numerous improvements, as with any technological advancement, new cybersecurity risks arise. An important part of the federal government IPv6 status in 2023 is a growing awareness of these risks. The National Security Agency has published guidance to help agencies anticipate and address these risks, particularly as they implement the IPv6 mandate and begin using the protocol on their network.
About The Security Features of IPv6
You may have heard that IPv6 requires IPSec (IP Security), increasing its security over IPv4. However, this should not encourage complacency, particularly when it comes to the federal government IPv6 status at present. The two major reasons for this are that IPSec is no longer required, and secondly, the security features of IPv6, designed in the 1990s, may not be adequate to surmount the cybersecurity challenges of today.
NSA’s Guidance on IPv6 Cybersecurity
NSA begins their guidance by noting that any cybersecurity risks associated with IPv6 have the potential to impact the bulk of devices and software on your network. The cybersecurity risks, while always a concern, are most present when a network is beginning to transition to IPv6 or lacks experience with the protocol. Dual-stacked networks, meaning those running IPv4 and IPv6 at the same time, have further cybersecurity concerns, requiring security measures tailored to each network.
The auto-configuration feature of IPv6 creates privacy concerns, by linking a device’s actions to that device and its user. To combat this, NSA recommends either using a Dynamic Host Configuration
Protocol version 6 (DHCPv6) to assign addresses, or employing a randomly generated interface, which will make it harder to associate activity with a specific device and user through ongoing changes.
As discussed above, tunneling can be a feature of the transition to IPv6, and the tunnels can be established automatically. Some transitions may even require tunneling. Unfortunately, the tunnels can also be a path for cyber attacks. The recommendation of the NSA is to block tunneling protocols and disabled tunneling on all devices on the network, unless tunneling is absolutely necessary and set up intentionally.
For dual-stacked networks, the basic idea is to make sure that when security measures are implemented on the IPv4 elements of your networks have an equivalent in the security measures on the IPv6 elements of your network. The security measures for each may not use exactly the same mechanism but they should each be at least as effective as the other.
NSA points out that one difference between IPv4 and IPv6 is that the latter lends itself to having multiple addresses assigned to the same interface. Cautioning that this increases the attack surface, NSA advises carefully evaluating whether your ACL is only allowing authorized traffic through your security measures, and making sure you keep an accurate traffic log and regularly check that the log reflects that only traffic that should get through is getting through.
The NSA guidance further explains the importance of training network administrators in IPv6, noting that configuring it incorrectly could make your network more vulnerable to cyber attacks.
These are the primary security risks and corresponding recommendations contained in the NSA guidance. The complete document addresses such issues as the use of Split DNS, filtering IPv6 traffic, local link protection, and concerns about translation between protocols and addresses.
The main takeaway from the new NSA guidance is to take cybersecurity issues around IPv6 seriously. This means that as agencies work to comply with the IPv6 mandate, they must provide specific training to network administrators, and facilitate the transition to and setup of IPv6 utilizing these best practices to mitigate the risk to your systems.
Stay Up-to-Date on The Federal Government IPv6 Status and New Cybersecurity Challenges with Sentient Digital
If you have yet to switch to IPv6, you can rest assured that this is the last IP switch you’ll ever have to make. IPv6 has a theoretically inexhaustible amount of IP addresses, promising your organization a sustainable, reliable platform for growth.
The long-term benefits of using the most affordable and universal Internet Protocol will make any growing pains worth it. At Sentient Digital, cybersecurity professionals provide federal organizations support for the development and management of organization-level assets compliant with NIST SP 800-53 requirements.
Ensuring IPv6-enabled spaces is one step towards optimizing industry practices from both the private and government sectors. Keeping up with federal standards is a crucial backbone to resource management, quality control, and risk and issue management, among other procedures and processes SDi implements to ensure that we provide the best possible support to our clients.
Contact us today to learn more about transitioning to IPv6 and other ways how our technology solutions can help you meet your objectives in areas such as cloud, cybersecurity, software development, systems engineering, and integration.




